CYBER DEFENSE AND PROTECTION
Cyber Defense and Protection is a coordinated set of actions to detect, analyse and prevent cyberattacks, and to react whenever necessary.
Taking back control
Reviewing and rethinking our practices, we have decided to reconsider and rethink our methods of Cyber Defense and Protection.
To carry out these projects, SEKOIA has gathered a multidisciplinary team that brings together advanced skills in development and analysis in an environment of increased agility: the Upscaling Team.
After several years of research and development, we reveal our new approach and the fruits of our labour.
—
Why implement Cyber Defense and Protection ?
Security incidents weaken value chains. They also raise awareness about the risks companies are exposed to both today and even more so in the future.
reducing exposure
The first stage in Cyber Protection and Defense consists in reducing risk exposure. Since risks are characterized by a combination of vulnerability X threat X impact, several approaches are possible. The capacity to PREVENT, DETECT, ANALYZE and REACT, are all concrete strategies that influence the way risks are characterised.
Prevent
detect
analyse
react
committed to the continuous improvement of our methods
While the benefits of implementing a process of continuous improvement are widely recognized, the excellence of the threats in this field is enough to confirm the vital necessity of such continuity. The methods, biases and technologies used by malware of all sorts continue to evolve and innovate incessantly. To protect and secure one’s assets therefore becomes a continuous task which affects every level of responsibility and concerns every structure of an organization.
respecting rules and regulations
Apart from the merits of our work as far as security is concerned, conforming to the demands that regulate the sector in question directly contributes to consolidating business activities and relations with clients and partners.
Three main problems that direct our efforts, and three axes of response :
Staff shortages
in cybersecurity teams

Allowing human integration
at the right level,
by eventually allowing the highest executive levels to act upon the lowest functional levels (minimizing the number and qualification of users by providing assistance and the keys to understanding the threat, to accompany decision making, implementation and follow-up of operations …).

Optimizing human capital
through automatization

Increased complexity
and growing interdependency

constraining threats by promoting
across-the-board data sharing :
Making the technology available both on a functional level (convenient use and adequate results) and on a material level (reducing or suppressing development and maintenance costs for the user, over time allowing the adjustment of resources to changing contexts and budgets).

Deteriorating
the flexibility of the attacker
by promoting sharing

Response time
is too long

capacity optimisation by upgrading info
and merging resources
+
allowing for fine-tuned contextualisation
of data processing, with the aim of producing adequate and adapted actions.

Making the most of current
and future capacities
through integration

The need
for an integrated
and adaptive
approach

The quality of protection depends not only on the performance of this or that function, but on the capacity of the entire system to integrate functions and provide the best possible protection and reaction to threats.
Cyber Defense and Protection must be approached globally, constantly and durably.
A systemic approach is key, and is the best way to respond to the specific professional challenges of each new problem encountered in the field.
Grasping the essence.
How to sum up this fight ? What are we doing today, what were we doing yesterday, and what will we continue to do tomorrow? Which main principles can make us more efficient, whatever the technological solutions of the moment may be ?
As a reply, SEKOIA has identified the key elements and stages of an integrated and automated Cyber Defense and Protection process. This constitutes the basis on which we have built an elementary and inter-operational architecture that supports and integrates every stage in the management of large quantities of data, from observation to remedial action.
As a starting point we chose to found our approach on a fundamental principle underlying any efficient chain of actions : the OODA loop.
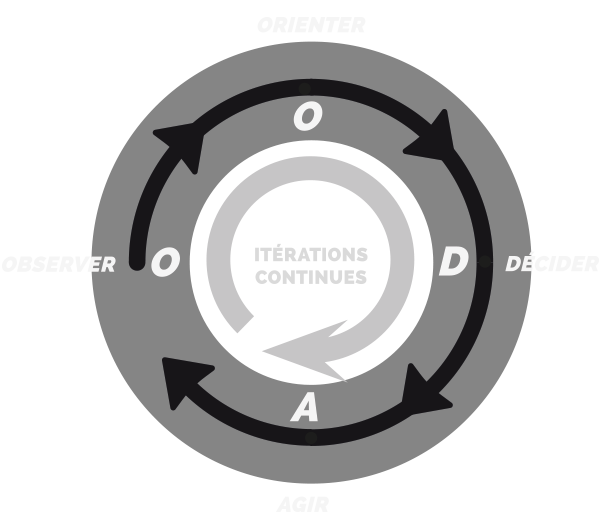
This framework was proposed by John Boyd of the US Air Force in 1960, and defines the key stages that need to be controlled in case of confrontation, and that can be executed faster than those of the adversary.
—
This logic of repetition is particularly appropriate for the operational aspect of cyber defense: speed is an index of performance, while the quality of the reaction triggered by the process can be improved during further cycles.
—
The three main factors of the speed
and range of cyber defense systems :
To go from theoretical plans to a functional system that is capable of executing chains of actions has required the elaboration of three main principles underlying the speed and range of cyber defense systems :

orchestration
Connecting security tools and integrating disparate security systems to take control of the automatization of the security system.

sharing indicators
Encouraging mutual sharing while also increasing the operational efficiency of shared indicators.

PLAYBOOKS
Synchronising the machine’s actions and aligning them with professional priorities and their matching specific operations.
Managing these three key factors at every stage of the treatment process allows us to exploit the complementary nature of specialized protection tools, to orchestrate them and most importantly, to continually enhance them by dynamically exploiting Threat Intel databases.
From the theoretical model
to the operational system :
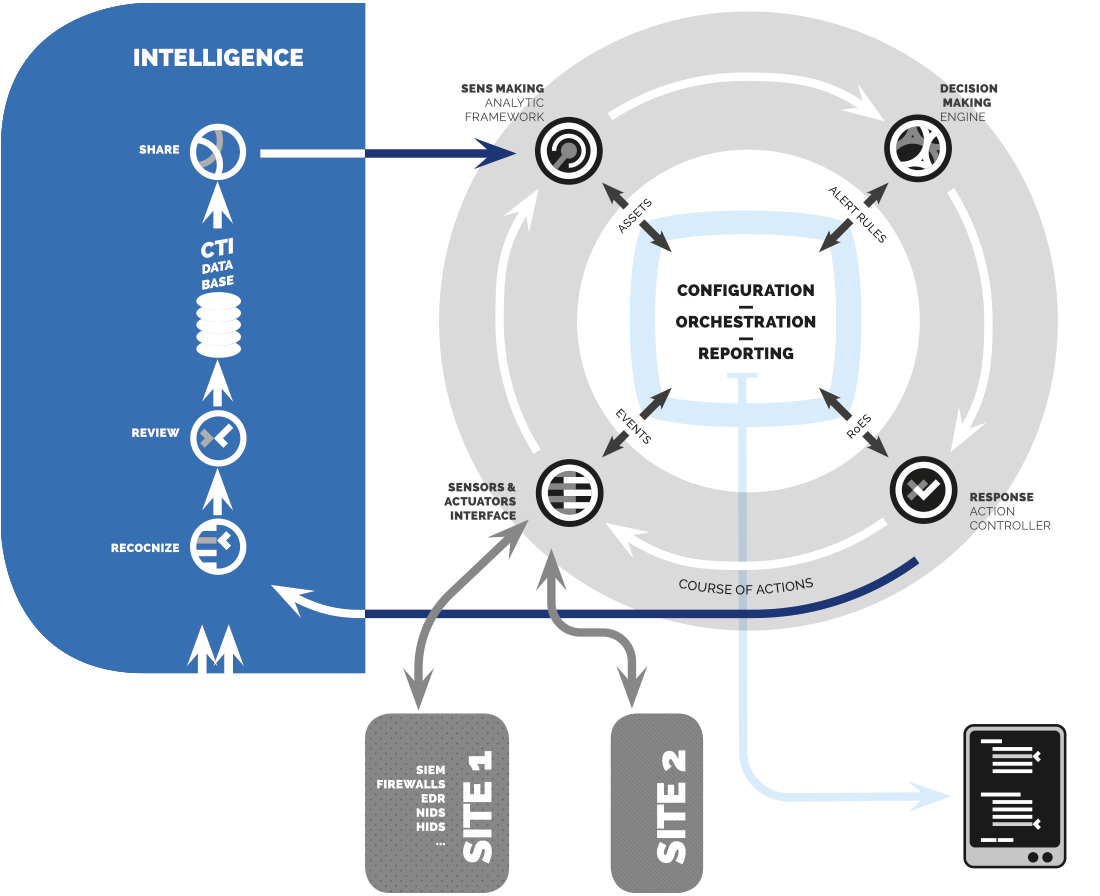
This timeless architecture includes functions able to handle the innovations of the future, benefiting from a synergy of interconnected and organized resources.
SEKOIA operates this new model of Cyber Defense and Protection, conceived in a systemic approach and based on Threat Intelligence management.
A repetitive loop involves a series of operations that are enhanced by a parallel exploitation process of threat intelligence :
observation
standardising interfaces for communication with the equipment (STIXv2 & OpenC2)
direction
adding meaning to information by contextualising and exploiting knowledge about threats, in order to improve understanding and evaluation of risks.
decision
implementing rules for detection, proposing the most adequate remedial strategies to match the results.
action
implementing remedial strategies by producing contextualised Courses of Actions.
—
SEKOIA applies
these principles
and innovates in the development, co-design and co-development of professional solutions.
—
INCREASED CAPACITY
In January 2019, SEKOIA reveals SEKOIA .IO, a solution in Cyber Defense and Protection in production since 2018.
SEKOIA.IO draws on a new doctrine in the design, integration and implementation of new means of protection.
SEKOIA.IO is an operational platform founded on our capacity to benefit from threat intelligence in order to dynamically integrate it in an innovative approach to Cyber Defense and Protection.
NEVER WAS SO MUCH OWED BY SO MANY TO SO FEW —W. Churchill.





